Domestic Internet traffic traveling inside the borders of Russia has repeatedly been rerouted outside of the country under an unexplained series of events that degrades performance and could compromise the security of Russian communications.
The finding, reported Thursday in a blog post published by Internet monitoring service Dyn, underscores the fragility of the border gateway protocol (BGP), which forms the underpinning of the Internet’s global routing system. In this case, domestic Russian traffic was repeatedly routed to routers operated by China Telecom, a firm with close ties to that country’s government. When huge amounts of traffic are diverted to far-away regions before ultimately reaching their final destination, it increases the chances hackers with the ability to monitor the connections have monitored or even altered some of the communications. A similar concern emerged last year, when Dyn found big chunks of traffic belonging to US banks, government agencies, and network service providers had been improperly routed through Belarusian or Icelandic service providers.
The hijacking of Russian traffic is linked to last year’s peering agreement between Russian mobile provider Vimpelcom and China Telecom. The pact allowed the firms to save money by having some of their traffic carried over the other’s network rather than through a more expensive transit operator. On multiple occasions since then, according to Dyn, communications destined for Russia has followed extremely round-about routes that take the traffic into China before sending it on to its final stop. Doug Madory, director of internet analysis at Dyn, wrote:
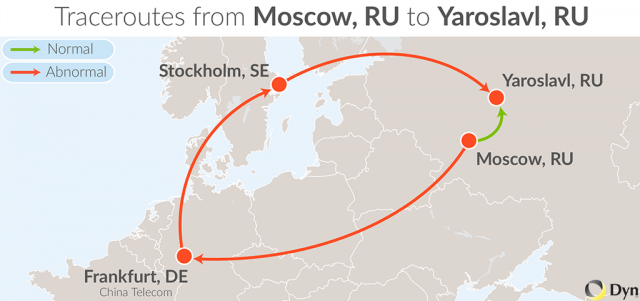
Even Internet paths from Moscow to other parts of Russia were forced through China Telecom’s routers. In the following example, a traceroute from Moscow is taken by Vimpelcom to Frankfurt, handed over to China Telecom’s routers in Frankfurt and, (mercifully) redirected back into Russia via Megafon without getting directed out to Shanghai. (This diversion of domestic Russian traffic is illustrated in the graphic at the beginning of this blog.)
trace from Moscow, Russia to Yaroslavl, Russia at 13:13 Aug 05, 2014
1 *
2 194.154.89.125 (Vimpelcom, Moscow, RU) 0.542ms
3 79.104.235.74 mx01.Frankfurt.gldn.net 37.006ms
4 118.85.204.57 beeline-gw4.china-telecom.net 39.505ms
5 213.248.84.185 ffm-b10-link.telia.net 41.481ms
6 62.115.137.180 ffm-bb2-link.telia.net 42.227ms
7 80.91.251.159 s-bb4-link.telia.net 42.894ms
8 213.155.133.105 s-b2-link.telia.net 41.528ms
9 80.239.128.234 megafon-ic-151430-s-b2.c.telia.net 42.707ms
10 *
11 78.25.73.42 (MegaFon, Volga,RU) 49.992ms
12 213.187.127.98 ysu1-ccr1036-1.yar.ru 50.301ms
13 213.187.117.230 (NETIS Telecom, Yaroslavl’, RU) 54.769ms
BGP is such a complex framework that improper routing of this type can often be the result of human error by engineers acting in good faith. But the same complexity and lack of security can just as easily be abused by hackers, government snoops, or vandals. Madory recommends operators of large networks carefully monitor the routes their traffic traverses and to filter the routes they receive. “Without both measures, your traffic could be easily misdirected, potentially hurting both the performance and security of your Internet communications,” he warned.
Article updated to edit headline.
Article source: ArsSec http://feeds.arstechnica.com/~r/arstechnica/security/~3/U1BFGTWtovo/